All bughunters want to find a P1 bug. But P1 bugs are not easy to find! Is that a true approach? I belive that if you ask full bug hunter they will say NO! To summarize it simply, probably they will say “thinking different will take you to P1 bug”. If you are doing everytinhg what other do probably you will never find P1 bug. Most P1 bugs start with an enpoint, files or folder. So discover sensitive endpoints, files, data, folders and more?
There are hundreds recon tool to find enpoint, files, or folder. We will review the ones that are easy and simple to use. Lets start with single easy js code.
Note: This article does not explain how to install the tools!
1. Click here to download the js or copy from below.
javascript:(function(){var scripts=document.getElementsByTagName("script"),regex=/(?<=(\"|\'|\`))\/[a-zA-Z0-9_?&=\/\-\#\.]*(?=(\"|\'|\`))/g;const results=new Set;for(var i=0;i<scripts.length;i++){var t=scripts[i].src;""!=t&&fetch(t).then(function(t){return t.text()}).then(function(t){var e=t.matchAll(regex);for(let r of e)results.add(r[0])}).catch(function(t){console.log("An error occurred: ",t)})}var pageContent=document.documentElement.outerHTML,matches=pageContent.matchAll(regex);for(const match of matches)results.add(match[0]);function writeResults(){results.forEach(function(t){document.write(t+"<br>")})}setTimeout(writeResults,3e3);})();Open the target in any browser and inspect it. Find “console” tab, paste the js and enter. That’s it!
Dont worry about errors. You can see many different enpoints which you can’t detect with any dirsearch tools. All fetched from js and any other data in the target url.
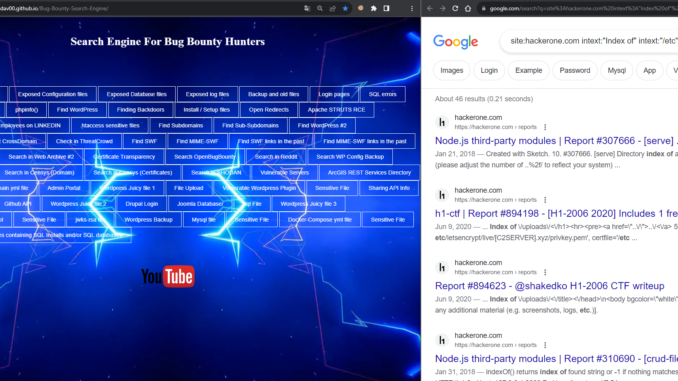
2. Search Engine For Bug Bounters
This one is just searcing data on google for you. I hope the owner will not delete the page. It’s almost like a night club full of fantasy. Click here to go there.
Just typ scope domain/url/ip and search it. The web page will filter your search on google. Here is an example. The target is hackerone.com and we clicked “Sensitive File”. It searches for “intext:” thats why we have got many results. Why not clicking all buttons?

Well here is a similar JavaScript file you can edit it.
GoogleDorkEngine
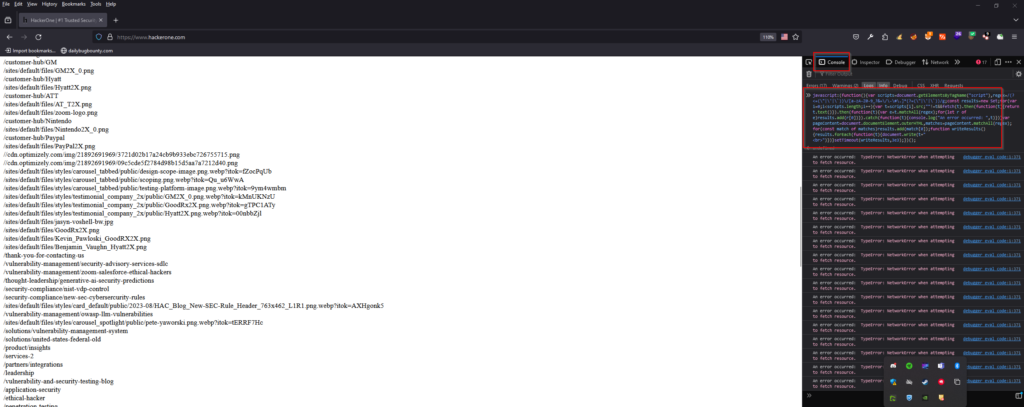
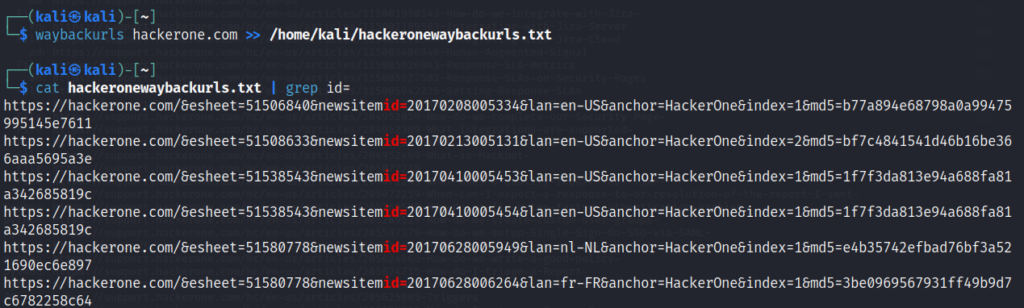
3. Waybackurls
No need to explain what is wayback to bug hunters. Its also easy way to discover sensitive endpoints, files, data, folders and more. Just run the commands bellow.
waybackurls hackerone.com >> /home/kali/hackeronewaybackurls.txt
After that you can grep with potential keywords.
4. Power Of Regex / SecretFinder (Yes its just regex actually)
This one is actually not to find only endpoints its also finds sensitive information. There are many ways to find JS files. You can use katana, waybacks, sudomy, or you can analyze the website manualy and extract JS urls.
Its not easy to read all JS files. Well for specific vulnerabilities sometimes we need. Bu in this case SecretFinder will analyze the js files with regex and will give us some potential data.
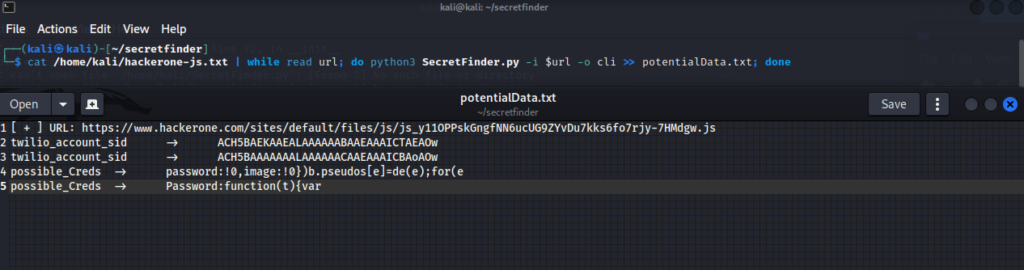
First install the SecretFinder and just run the command below.
I saved all my JS files to hackerone-js.txt. After running the command below it will extract potential data for me to potentialData.txt.
┌──(kali㉿kali)-[~/secretfinder]e
└─$ cat /home/kali/hackerone-js.txt | while read url; do python3 SecretFinder.py -i $url -o cli >> potentialData.txt; don
There could be many false positives, but at least it will be human readable.
Notes: The creator of Bug-Bounty-Search-Engine is NitinYadav00. Thanks for contributing the community!
Dont forget to grep words below
“redirect=”
“api” “token”
“@”
“user”
“logout”
“admin”
“number”
“redirect=”
“.txt”
If you dont know how to use linux commands. Just check this page.
Leave a Reply