A thread🧵
💸Secrets of automation-kings in bug bounty💸
Finding 1day (or 1month) web exploits that haven’t made their into scanners yet can make you big money.
Read more to understand where and how to get an edge in this area!
🚨🚨
1/x A competitive advantage in bug bounty is being able to write your own vulnerability checks.
There are hundreds of COTS and OSS software that have vulnerabilities that never end up in a vuln scanner because of various reasons…
2/x Maybe because the software isn’t a big name like Microsoft or JIRA. Maybe the vendor & the reporter don’t make any fanfare about the bug.
Whatever the reason, you can profit by making your own checks! This has never been easier with tools like @pdnuclei and Jaeles!
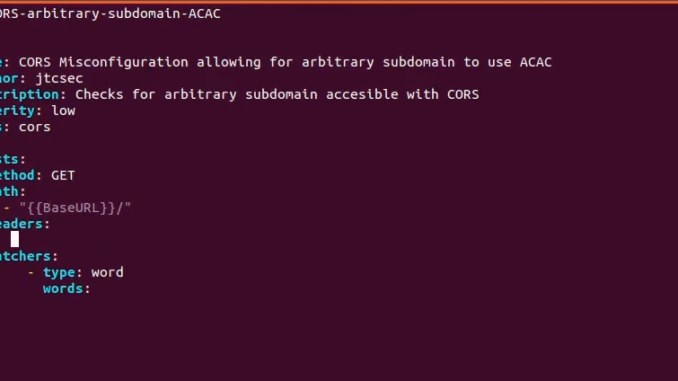
3/x For Nuclei, you can create these templates using YAML and the Nuclei template guides here:
nuclei.projectdiscovery.io/templating-gui…
4/x
https://nuclei.projectdiscovery.io/templating-guide/.@jtsec has a video guide for those interested where he creates a custom CORS check:
5/x For Jaeles by @j3ssiejjj you can follow the documentation at:
jaeles-project.github.io/signatures/exa…
If you’re unfamiliar with Jaeles, here’s a quick demo:
6/x
https://jaeles-project.github.io/signatures/examples/I use nuclei for a lot of misconfiguration type checks and CVEs. I use Jaeles more for custom web fuzzing.
So now you know how to make a check… how do you know what to make?
Surprisingly Twitter can be one of the best intelligent sources for this!
7/x I’ll walk you through how I and some others do this.
1st you’ll need a separate Twitter account.
Once you have that head over to tweetdeck.twitter.com!
We’re going to use Twitter live searches to find CVE’s and exploits to make into templates for our scanners.
8/x I have a column in TweetDeck that represents a live search for each vulnerability type in existence. For example, I’ll get you started:
9/x One of my columns is a live search for:
“local file include” OR “path traversal” OR “directory traversal” OR “arbitrary file read”
10/x another is:
“Broken Authentication” OR “Authentication Bypass” OR “account takeover” OR “Sensitive Data Exposure”
I have over 30 live searches running in TweetDeck to update me on new CVE’s, vuln classes, and writeups, which I can then port into vulnerability checks!
11/xAnother source of vuln intelligence in parsing Bugcrowds disclosures and Hackerone’s hacktivity pages.
Read the writeups and if one seems like a good check or novel fuzz string, add it to your arsenal.
12/x
Managed bug bounty programs, a better approach to securityBugcrowd’s bug bounty and vulnerability disclosure platform connects the global security researcher community with your business. Crowdsourced security testing, a better approach! Run your bug bounty …https://bugcrowd.com/crowdstream
https://hackerone.com/hacktivityWhat’s the UBER level of this?
I know two hunters who pay for subscriptions to Threat Intelligence feeds as an upfront cost. These feeds often have inside info on CVE endpoints that are not public yet, including PoC fuzz strings. They make templates from them and profit.
13/x With a constant, automated, scanning routine you can build a monster vulnerability scanning machine!
You should look into Axiom by @pry0cc as the glue that can scale an operation like this 😉😉😉:
14/x
https://www.youtube.com/embed/t-FCvQK2Y88
https://www.youtube.com/embed/tWml8Dy5RyMThat’s it for now, did I miss anything?
A full and expanded blog with MORE & ALL links for this thread will be on my blog in a few days:
✌🏻For more resources follow, retweet, & like!✌️
https://twitter.com/Jhaddix
Leave a Reply